Security experts have two common laments:
- Security is an afterthought, and
- Security is hard to get right.
No place else has this been more true than in wireless security, where it took the better part of two decades to get us to where we are today. “Wireless” can mean many different things. It could mean 3G cellular service or Wifi or Bluetooth or something else. In the context of Wifi, we have standards such as WPA Personal and WPA Enterprise that were developed at the IEEE. Similarly, 3GPP has developed secure access standards for your phone through the use of a SIM card. With either WPA Enterprise or 3G, you can bet that if your device starts to misbehave, it can be uniquely identified.
Unfortunately that’s not so much the case with other wireless standards, and in particular for IEEE’s 802.15.4, where security has for the time being been largely left to higher layers. And that’s just fine if what we’re talking about is your Bluetooth keyboard. But it’s not fine at all if we’re talking large number of devices, where one of them is misbehaving.
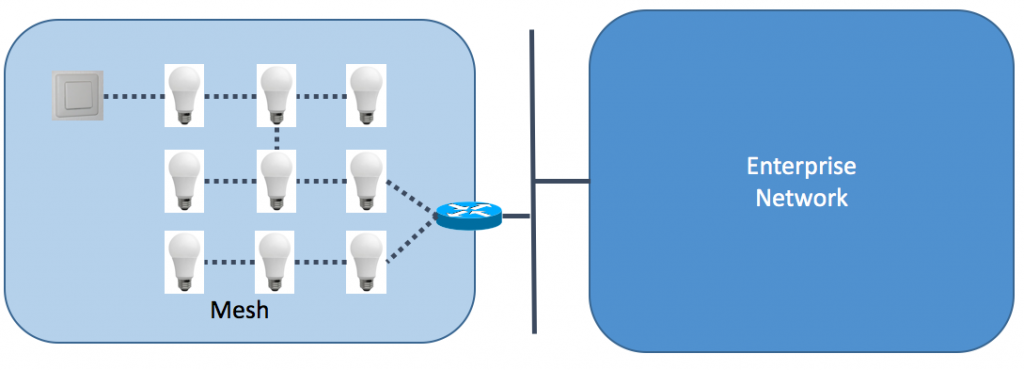
Here we have a lighting network. It might consist of many different light bulbs. Maybe hundreds. Now imagine a bad guy breaking into one of those devices and attacking the others. Spot the bad guy. In a wired world, assuming you have access to the switch, you can spot the device simply by looking at which port a connection came into. But this is wireless, and mesh wireless at that. In the case where each device has its own unique key, you can trace per session per device. But if all devices use a shared key, you need to find other means. A well hacked device isn’t going to give you many clues; it’s going to try to mimic a device that isn’t hacked, perhaps one that isn’t turned on or one that doesn’t even exist.
These attacks can be varied in nature. If the mesh is connected to other networks, like enterprise networks, then attacks can be aimed at resources on those networks. This might range from a form of a so-called “Snow Shoe” attack, where no one device generates a lot of traffic but the aggregate of hacked devices overwhelm a target, to something more destructive, like attempts to reconfigure critical infrastructure.
Some attacks aren’t even intended as such, as Raul Rojas discovered in 2009, when a single light bulb took down his IoT-enabled house.
What to do?
The most obvious thing to do is not to get into this situation in the first place. From a traceability standpoint, network managers need to be able to identify the source of attacks. Having unique wireless sessions between leaf and non-leaf nodes that are bound to source addresses is ideal. Alternatively, all communications in a mesh could tunnel to non-leaf nodes that have strong diagnostic capabilities, like IPFIX and port spanning. At that point administrators can at least log traffic to determine the source of attacks. That’s a tall order for a light bulb, but it’s why companies like Cisco exist- to protect your infrastructure.
If none of these alternatives exist, poor network administrators (who might just be home owners like Mr. Rojas) are forced into a position where they might need to consider the entire mesh a single misbehaving device, and disconnect it from the network. And even that might not do the job: a smart piece of malware might notice and quiet itself until it can determine that the mesh has been re-connected.
Some careful thought is required as these capabilities develop.