A number of security researchers are getting upset by seeing home devices communicate with one another or with random sites in China. Is this an attack? Probably not. But there may be vulnerabilities that can be exploited that should cause consumers pause.
There are two common design patterns. Today I’m just going to discuss what we call “Calling Home”. When we use the term, we are not referring to your home, but to a centralized management site. In the case of Thing manufacturers, the site is likely offered by the manufacturer.
So you just bought that new digital video recorder and it offers a great new feature: you can program it wherever you are. There are many such devices on the market today, such as a SlingBox. How do those communications happen?
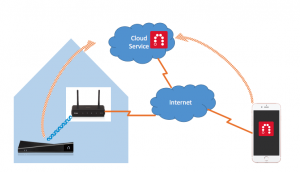
In the figure above, all your home devices sit behind your home router. They’re generally allowed to connect to systems outside of your network, but systems outside are not able to connect in. In part this is a security feature: your firewall will block incoming connections so that the entire world can’t attack you. In part, however, it’s because the systems in your home are only using locally recognizable IP addresses. And since your iPhone moves around, your home doesn’t know how to get to it. Therefore, a rendezvous service is needed. That’s what that cloud function is performing, and that is what those curved lines indicate.
The SlingBox on the left may not just be connecting for the sake of communicating with your smart phone. It is probably also doing so for other reasons, such as receiving electronic program guide information.
In the world of IoT, that is a common design pattern. Devices will need to communicate with their manufacturer web sites for all different reasons, but there is one common and important reason: devices will have bugs. As manufacturers develop fixes, devices will need to learn of those fixes and install them. Every modern-day operating system and browser has this feature. All Things will need these features as well. In fact, one big concern today is what happens when manufacturers do not offer fixes? Then those vulnerabilities are out there for anyone to exploit. This is a big problem in the developing world, where consumers often buy devices on the secondary market, long after manufacturers have intended them to be retired.
Could a device transmit private information to a manufacturer? Sure. In fact, Samsung got caught last year through their dreadful privacy policy where their televisions could have been listening and reporting conversations.
Here’s the rub: without extensive analysis, it’s hard to know exactly what is being exchanged between a device and a manufacturer. Encryption will keep observers from seeing what is being exchanged. At the same time, a lack of encryption would be as or more risky to consumer privacy.
When devices are able to communicate at all it is possible that they will be compromised. It’s important to understand that there are risks with each Internet-enabled device. But it’s also important to consider any benefit the communication will have. A refrigerator or a heater that knows it is in need of repair can have a manufacturer contact the owner, for instance. That’s worth something to some people. Judge the risks for yourself.
What should the best practices be in this space and what should consumers expect in products? More on that over time, but feel free to answer those questions yourself for now.
iPhone image courtesy World Super Cars on Wikipedia.