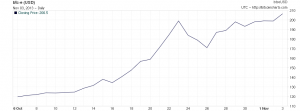
For those who don’t know, BitCoin is an attempt at a new type of currency, one that isn’t linked to any nation. In a way, bitcoin is a lot like gold or other commodities, only it differs in that you don’t actually have to ship anything around or even keep trading futures to stay in the game. Still it accrues similar benefits as gold. In fact there is a bitcoin to gold price, based on milligrams of gold.  As you can see the number of milligrams one gets for a bitcoin has gone from about 300 in January to about 3,300 in October. Bitcoins have clearly paid off for some people.
As you can see the number of milligrams one gets for a bitcoin has gone from about 300 in January to about 3,300 in October. Bitcoins have clearly paid off for some people.
One of the other goals of bitcoin is that they be as anonymous as cash. This is where the problems start. Let’s say you want to sell a few bitcoins, and receive American dollars. One question is simply this: do you have to list the sale on Schedule D? I am no accountant, but I would think the answer would be “yes”. Now let’s say that instead of selling them, you are just holding them, and let’s for the sake of argument say that you have $500,000 worth of bitcoins. Do these represent foreign assets? If so, you are required to file forms with both the Treasury (TD-F 90-22.1) and the relatively new IRS Form 8938.
Those who in any way behave like banks will find that the Treasury department expects them to do all the things banks do. That includes reporting on suspicious transactions or any transaction over $10,000.
This hasn’t stopped people from attempting to hide transactions. Here’s an article from CNN about a guy who attempted to do all sorts of nasty things with Bitcoins. This led to a huge drop in their value, almost overnight.
So, now the question: are bitcoins here to stay or are they a passing fad (read: pyramid scheme)? The entire technical premise of bitcoins is in fact that they can be anonymously traded. The bad news for people with bitcoins is that because there is no single management point that has guns (thus differentiating them from a classic currency), unless the likelihood is that those with the guns will want to limit or prohibit this sort of transaction; especially in large quantities.
A similar situation arose in 2001 when the U.S. government began to crack down on those using the old mechanism known as Hawala, even though the mechanism is legal. And so one question is simply this: are bitcoins really anonymous? A researcher named Sarah Meiklejohn will present a paper at SIGCOMM this month on just what law enforcement capabilities there are. Watch that spot.
 I am no fan of the Muslim Brotherhood, as many of their political positions are diametrically oppose to my own.
I am no fan of the Muslim Brotherhood, as many of their political positions are diametrically oppose to my own.