Really it’s not clear to me if this is a generational thing or what, people tell me that email addresses are no longer that important to them, what with MySpace, FaceBook, and the like. Others just use SMS, where their cell phone number is the important for people to reach them. For some, however, their email address is their identity, and their only means of being reached by friends and family. That’s true for me, at least. I’ve had the same sets of email addresses for about 12 years– one for work, one main one for play, and a bunch of others for special use. This is nothing compared to my parents, who have had (roughly) the same phone number for almost forty years.
If your email address is important, here’s a question you should ask: is it important for you to control it from a legal standpoint? Why would you want to do this? Let’s look at a few cases:
- Your Internet Service Provider (ISP) provides you your email address with your Internet service, be that DSL, Cable, or something else. What happens if you decide to change ISPs? Do you lose your email address? And do you care? Can someone else get your old email address, and what are they likely to receive?
- You have a free email account from a service like Yahoo!, MSN, or Google, and the account gets broken into. The first thing the bad guy does is change all of the security questions that are meant to cover password recovery. How, then, are you able to prove to the service provider that the account was yours in the first place? Can you even get your old account shut down, so that the attacker can’t masquerade as you?
- This is the inside-out version of (2): suppose someone claims you are masquerading as the legitimate owner of your account? Who do you go to in order to prove that you are the legitimate owner of the account?
- Your mail service provider goes out of business, and the domain they have been using for you is sold.
- There’s one special case I’ll mention, but let’s not try to solve it: you use your work email for all email, and you change jobs or are laid off. It’s a safe assumption that the primary use of your work email account should be work, and that you are taking a risk by using the account for more than work.
For all but the last case, you have a way of at least mitigating the problem by have your own domain name, like ofcourseimright.com. That is- go to a registrar that you trust and choose a domain name that will be yours as long as you pay the bill for the domain. However, is this just moving the problem? It could be if someone breaks into a registrar account that is not well secured. However, because you own the domain and the registrar does not, you are able to take at least some actions, should either your registrar not recognize you, or should your registrar itself go out of business (this has happened).
The hard part is finding someone to host your domain. This sounds like a royal pain in the butt. And it is! So why not just use your cell phone or a social network site? Cell numbers are at least portable in many countries. Social networking like Facebook is another matter, and can leave you with many of the same problems that email has, and more, as we have seen. Similarly, many financial services that play with your money, like PayPal and eBay, rely on you having a stable email address.

Loading ...
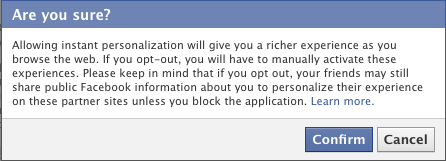
![]() Here is a really good article from the Electronic Frontier Foundation (EFF) about deceptive user interface practices. The funny thing about all of this is that people are missing the most offensive and dangerous part of Facebook’s warning:
Here is a really good article from the Electronic Frontier Foundation (EFF) about deceptive user interface practices. The funny thing about all of this is that people are missing the most offensive and dangerous part of Facebook’s warning: